Developing ICAM Experiences As A Learning Canvas
Learning and implementing a better and more secure experience pertaining to identity, credentialing, and access management has been something of a mild adventure. From reviewing the specifics of FIDO2, to attending a few security and identity workshops/conferences, there’s this sense I’m one part behind the ball in learning. And yet while looking at the pace of practice/implementation/policy, there feels like a sense of being ahead. This felt crystallized best when asking around the question: “what’s the difference between security and a secure experience?”
People way more qualified than I have answered, broken, and re-answered this question many times. Attention on “experience” by the FIDO Alliance has stuck out most notably. 🙌🏽 The mathematical models aren’t the issue (usually) - it is about what people do or don’t do which starts and caps what’s perceived as security. Digging into a bag of conceptual scribbles, I started looking first at simpler actions (logging in, continual auth, reporting, etc.), and then later into fuller concepts (“you do this action, what are you expected to do/decide”).
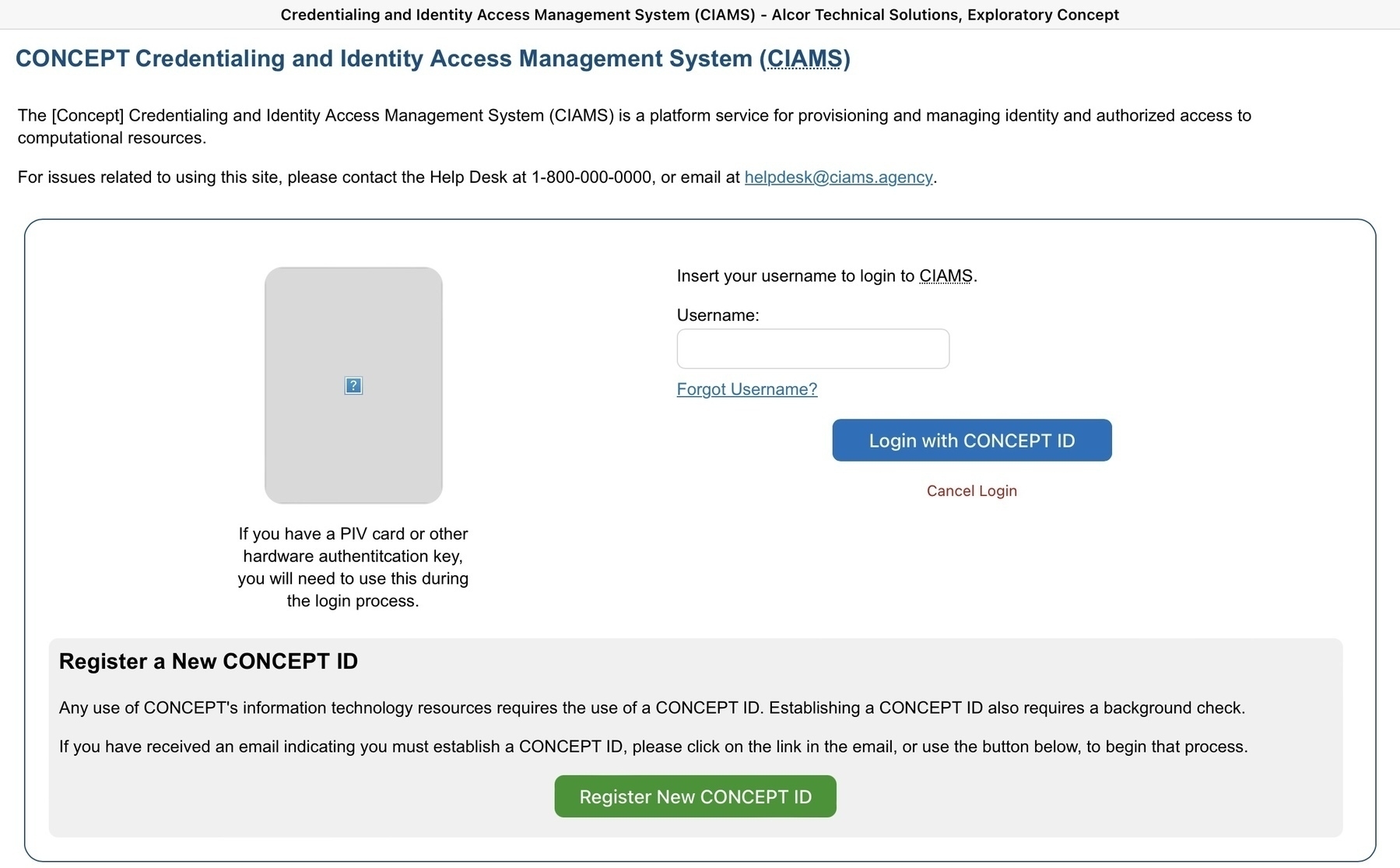
This led to a working-concept exploring front-end interactions - instigating questions to drive user, developmental, and business decisions - called the CIAMS Concept. The CIAMS Concept was kept simple with plain HTML, CSS, and JS preventing abstractions caused by various libraries from impacting my learning. Obviously, this caused some unique problems such as: “how do you solve for a dynamically generated QR code for passkey demos” or, “what shouldn’t be answered by here but should be shown to ensure it happens in a backstage action?” Each iteration of the concept led to some targeted learning through platforms like Radiant Logic, ForgeRock, Login.gov, Okta, and more. It opened questions similar to what FIDO Alliance answers in their assortment of case studies. And eventually expressed answers in rough, yet convincing terms.
It also had the impact of shifting how operationally to think about the impact of developing an ICAM (identity, credentialing, and access management) platform or following thru on its implementation. Change management comes very close to the desk of UX solution architects (or should I use the newer term “design engineers”). How people observe what will change and what is profitable to communicate or train, versus what should become a delightful revelation is part of the mapping of a security experience in ways which seem different from older conversations. Designers I work alongside are embracing service design just as much as they are design systems because the interactions are where security is judged - not necessarily the inputs or outputs. This adds to the plate of what’s important to know - and even more to what’s important to implement. Great quote on Twitter/X recently to this last bit: “…Your designs are only as good as their implementations.”
Driving on that road between concept and implementation has been the summary-lesson of this effort as well. As much as it has been a beautiful exercise to create this ICAM concept, putting it in such a posture where it could aptly demonstrate ICAM principles while simultaneously providing guidance to requirements or implementation has been (insert whew emoji). You find the layers of what’s understand about the tooling but not about the usage. Or, what might be conceptually clearer on one platform/modality than another. Given my penchant for jumping into some modalities well-before others conceive them outside of their imaginations, it is even more insightful to what feels like it should be a solved problem.
Some other conclusions from this experiment/exercise:
- the pace of passkey implementations really has been helped by coordination between Microsoft, Apple, Google, etc.
- some of what’s coming down the pipe in hardware (especially “AI Hardware”) breaks previous conventions (see “how to enter a WiFi password on the Humane AiPin” as one clear example)
- the enterprise shift towards data visualizations can sharpen some security contexts, but the nuances of how to create and understand dynamic thresholds for various policies will be more of a challenge
- there are so, so many parameters, protocols, certifications, to keep up with that it might actually be smarter to keep up with identified behaviors and filter the other bits from there
- as an industry, ICAM seems to be commoditized; but the pace of implementations makes that harder to see in some contexts more than others
And probably my favorite lesson - curiosity seems to be where the canvas answers the difference between security and secure experiences. Not just one answer, but many, each with advantages and trade-offs. Will be very interesting to see how this evolves as JSON .canvas and spatial computing appliances approach wider usage. Some of those newer modalities enabling secure expressions for the kind of usage we desire from productive and secure computing practices. Maybe federation moves from the niche to the norm. Or maybe the negative hand of surveillance becomes the hoodie we cannot help but to adorn ourselves in.
Feels ahead and behind at the same time to be back at exploring like this. I’m scribbling to push even further.